FIG. 23.2 The NIC naming tree.
| Previous | Table of Contents | Next |
Table 23.5 lists the pertinent RFCs for establishing a network. Some of these documents go into great detail about how the different protocols function and the underlying specifications and theory. Others are more general and provide key information that can be useful to a network manager. At a minimum, an Internet network manager should know where these documents are located and how to obtain them. They provide information that can help in planning and growing an organization’s network.
| RFC Name | Description |
|---|---|
| RFC791.txt | Internet Protocol DARPA Internet Program Protocol Specification |
| RFC792.txt | Internet Control Message Protocol |
| RFC793.txt | Transmission Control Protocol DARPA Internet Program Protocol Specification |
| RFC950.txt | Internet Standard Subnetting Procedure |
| RFC1058.txt | Routing Information Protocol |
| RFC1178.txt | Choosing a Name for Your Computer |
| RFC1180.txt | A TCP/IP Tutorial |
| RFC1208.txt | A Glossary of Networking Terms |
| RFC1219.txt | On the Assignment of Subnet Numbers |
| RFC1234.txt | Tunneling IPX Traffic Through IP Networks |
The naming of network nodes requires some planning. When you select names, keep network management and user acceptance in mind. Many organizations have network-naming standards. If your organization has such standards in place, it’s best to follow them to prevent confusion. If not, there’s plenty of room for imagination. Computer and network names can be as simple as naming the workstations after the users, such as Diane, Beth, or John.
If you have many similar computers, numbering them (for example, PC1, PC2, and PC128) may be appropriate. Naming must be done in a way that gives unique names to computer systems. Don’t name a computer thecomputerinthenorthoffice and expect users not to complain. After all, even the system administrator must type the names of computers from time to time. Also avoid names like oiiomfw932kk. Although such a name may prevent network intruders from connecting to your computer, it may also prevent you from connecting to your workstation.
Names that are distinctive and follow a theme work well, helping the coordination of future expansion and giving the users a sense of connection with their machines. After all, it’s a lot easier to have a good relationship with a machine called sparky than a machine called OF1284.
Remember the following points when selecting a naming scheme:
If you follow these guidelines, you can establish a successful naming methodology.
Internet names represent the organizations and the functionality of the systems within the network. Following are examples of names that you can use:
The following are examples of names that are difficult to use or remember:
The latter of these could be encoded information about a workstation in room 345 on network 56 with network executive functions, but this type of naming scheme is usually considered poor practice because it can lead to confusion and misdirected messages.
An Internet name such as Eddie@PC28.Programming.mycompany.com enables you to reference a user on a particular node
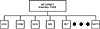
The NIC maintains a network naming tree. This tree is used to group similar organizations under similar branches of the tree. Figure 23.2 shows the naming tree. Major organizations are grouped under similar branches. This is the source for Internet labels, such as com, edu, and gov, that are seen in Internet names.

FIG. 23.2 The NIC naming tree.
Table 23.6 shows some of the common leaf names and definitions for the NIC tree. Many other leaves are under the tree, but these are the most common.
| Name | Types of Organizations |
|---|---|
| edu | Educational facilities (such as universities and colleges) |
| com | Commercial (most corporations) |
| gov | United States non-military government bodies (White House, Department of Agriculture) |
| mil | Military (military users and their contractors) |
| net | Internet network management and administration |
| org | Other types of organizations (usually non-profit) |
| Previous | Table of Contents | Next |