| Previous | Table of Contents | Next |
Hour 9
Ethernet Basics
You’re probably familiar with the classic battle BetaMax versus VHS, an example of a simple, more accessible technology (VHS) fighting with a complex, more elegant (and more expensive) technology (BetaMax). Some people like one, some people like the other, but no one can argue with the fact that the simpler technology dominates units sold and mind share.
You can chalk up another clash of the titans when you consider Ethernet versus Token-Ring, with Ethernet being by far the simpler and more popular technology. Some folks like Ethernet, some like Token-Ring. If Token-Ring is what you have, read on anyway—it’s good to know the differences.
Since I’ve already alluded to the fact that most networks are party lines—that is, lines with more than one network card talking on them—one obvious difference between different network types can be the way in which they share the line. That is, is it a free-for-all or are rules followed?
Not all Ethernet networking is party line based. A fully switched Ethernet network—that is, one with one workstation on each switch port—is actually composed of many two-person networks.A network with just two participants is called a point-to-point network, much like your PC’s connection with your Internet service provider.
Although most folks refer to a point-to-point network only when considering outside dial-up and leased lines, the defining quality of a point-to-point network is that there are only two stations on the segment. Once you introduce a switch into the picture, you actually only have two stations sharing a common line (the switch port and the PC), so it is a point-to-point network—that is, a network with only two end points. The switch then connects folks together much like the phone system does, without others listening or being able to interfere.
Following the Rules: As Long As You Live Under Our Network…
Ethernet is a party line with rules. They’re pretty basic and simple rules, but they’re rules, nonetheless. The acronym for these rules is CSMA/CD, which stands for Carrier Sense Multiple Access Carrier Detect. Just as you can listen even as you start talking at the same time another person starts talking, Ethernet network cards listen as they start to transmit to the party line. The carrier in CSMA/CD, like the dueling banshees you hear when your modem connects to another, is a predefined signal that information can ride on top of.
Collisions
If another network card is transmitting while your network card is also transmitting, the signal becomes garbled—the wire can only hold one signal at a time. This generates a network error called a collision. When a collision occurs, both network cards wait a random infinitesimal amount of time, and try again. Eventually, as shown in Figure 9.1, they do succeed, on a low-population segment. Because each workstation transmits in small, discrete packets (discussed in Hour 1, “The Telephone Analogy: Becoming Familiar with Basic Networking Concepts”), it’s possible (believe it or not) for a workstation to get a word in edgewise in between another workstation’s transmissions. This has always seemed like black magic to me, but it works.
At moment 1 in Figure 9.1, Vizzini and Fezzik simultaneously try to transmit and thus collide. They randomly retry, but it happens to be at the same moment (2). They retry again, and Fezzik gets in at moment 3, followed by Vizzini at moment 4. Poor Vizzini collides with Inigo at moment 4. Vizzini retries at moment 5, nobody does anything at moment 6, and Inigo finally gets the final word in moment 7.
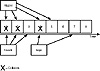
Figure 9.1 Collisions!
On a small network, collision detection works pretty well. But just as informal meeting rules start to break down when you get more than 10 or 15 people in a conference room, Ethernet, too, turns into a babble fairly quickly when a particular segment is scaled to more than a couple dozen workstations.
Ethernet is really, really easy to cascade; that is, you can extend the party line from a hub by simply adding a single cable and an additional hub. Instant upgrade, huh? Buy a hub and hook it up!
Although it’s easy to add a hub or two via cascade, you don’t want to go crazy on this. Be careful about how large your Ethernet gets—if you add too many hubs, you’re going to run into trouble.Many Ethernet installations in smaller shops have just sort of grown larger rather than having been designed that way from the ground up. This can result in lots of workstations sharing the same segment, which translates into lots of collisions. Take a look at your segment maps and count how many workstations are on each; for optimal performance and reliability, you’ll want to subdivide your segments into smaller divisions using a switch.
Framed and Fragmented
It’s worth briefly looking at the packet structure of Ethernet. Remember from Hour 1 that a packet is the smallest unit of transmission on a network. There are times when differences in packet sizes can cause problems between two network segments, so you should know the different maximum packet sizes of your networking topologies.
Ethernet’s maximum packet, or frame size, is 1,514 bytes. This includes six bytes for the MAC address of the source NIC, six bytes for the MAC address of the destination, a two-byte value indicating what kind of packet it is, and a “payload” portion that holds your data (this can be a maximum of 1,500 bytes). Some people (even those who design network analyzers) refer to a maximum value of 1,518 bytes. This number just includes a four-byte error-detection value at the end of each packet. Another 20 bytes of overhead can be found at the beginning of the packet (but this is only of interest to Ethernet switch designers).
Any Ethernet packet less than 60 bytes is considered a runt, also called a short or fragment, and will show up as an error on a software analyzer. A runt can be caused by collisions, so if you see a lot of these, you might want to consider dividing up your users among switches.
| Previous | Table of Contents | Next |