|
To access the contents, click the chapter and section titles.
Platinum Edition Using HTML 4, XML, and Java 1.2
(Publisher: Macmillan Computer Publishing)
Author(s): Eric Ladd
ISBN: 078971759x
Publication Date: 11/01/98

NOTE: Although Certification Authorities and X.509v3 certificates are emerging as the de facto standard, other systems are available. Phil Zimmermann’s PGP (Pretty Good Privacy) software, for example, is based on a “web of trust,” in which you are invited to trust an unknown person because people whom you know and trust either vouch for the unknown person or they vouch for people who vouch for the unknown person, and so on. Learn more about PGP online at http://www.nai.com/ and http://www.pgpi.com/.
Why Do You Need a Message Digest Algorithm? Another flaw is present in this system. Computationally, it’s inefficient to encrypt a large file, such as a JAR file, with a private key. Actual public key encryption systems don’t try to do this—instead, they apply an efficient algorithm called a message digest algorithm to produce a long number—one that is virtually unique to this message. Then they encrypt only the message digest itself.
One of the most common message digest algorithms is called SHA1; one of the most common public key encryption algorithms is called DSA. The rest of this section shows you how to sign JAR files with an SHA1/DSA-based signature.
The Java Utilities In addition to the jar utility, you’ll need two tools to sign JARs:
- • keytool—Used to produce public/private keypairs and certificates. For complete documentation on keytool, see docs/guide/security/spec/security-spec.doc17.html in your JDK directory.
- • jarsigner—Used to actually sign the JARs, based on your certificate. For complete documentation on jarsigner, see docs/tooldocs/win32/jarsigner.html in the JDK directory on your hard drive. (If you’re a Solaris user, a corresponding file in the solaris directory shows how jarsigner works on your machine.)
|
 | Both keytool and jarsigner are designed to be run from the command line—they’re simply wrappers around the Java classes that implement keys, certificates, and signatures. Sun provides a tool for users to use in setting their security policy—called policytool—that has a graphical interface.
|
|
Signing a JAR—Step-by-Step Here’s a step-by-step procedure for signing your JAR files. The remainder of this section describes each of these steps in detail.
- 1. Generate a keypair.
- 2. Obtain a certificate for your keypair.
- 3. Distribute your certificate so people will know that you’re the person behind the trusted applet.
- 4. Use your certificate to sign your JAR.
Figure 41.9 illustrates this process.
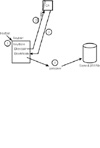
FIGURE 41.9 Use Sun’s tools to generate a keypair, request a certificate, install it, and sign a JAR file.
If you’ve already generated a keypair and obtained a certificate through another means (such as Netscape Navigator and the Netscape Certificate Server or Verisign, Inc.), you can skip the first two steps and go right to jarsigner. In the rest of this section we’ll assume you’re starting from scratch. In the first step, we’ll generate a keypair and a self-signed certificate. In the second step we’ll send off a Certificate Signing Request to the CA of your choice.
CAUTION: You could use a self-signed certificate to claim you were anyone. Sophisticated users will often ignore such certificates. For serious work on the Internet, consider having your certificate generated by a reputable firm such as Verisign (http://www.verisign.com/).
Generating a Keypair
Sun provides the utility keytool to administer databases of keys and certificates for use by the utility jarsigner. You can get basic usage information by typing
keytool -help
at the command prompt.
To generate a new key you might type
keytool -genkey -alias mike
This line tells the keytool to generate a new key to be stored under the name “mike.”
NOTE: Not enough information is in this line for keytool to generate a new key. It needs a Distinguished Name, a passphrase for the password itself, and a passphrase for the keystore. It will prompt you for any required fields you fail to specify.
When you generate a new keypair, you may include the following options:
- • -v—Produce verbose information.
- • -alias alias—A common name to be associated with this key.
- • -keyalg keyalg—Specifies the algorithm to be used for generating the key.
- • -keysize keysize—Specifies the size of the key, in bits.
- • -sigalg sigalg—Specifies the algorithm to be used for preparing a message digest.
- • -dname distinguishedName—Your personal Distinguished Name, which usually includes your organization and country.
|
 | The X.500 Distinguished Name uses commas to separate the fields. If one of your fields contains a comma, escape it with a \ character.
|
|
- • -keypass keypass—The passphrase for this key. If you don’t provide one, you’ll be prompted for it. The tool requires that the passphrase be at least six characters long—for better security, make yours much longer than that.
- • -keystore keystore—The location where the keys will be stored.
NOTE: If you allow keytool to put your keys in the default file, it will build a keystore in a file named .keystore in your home directory. On a Windows system your “home directory” is the concatenation of the HOMEDRIVE and HOMEPATH environment variables. If they’re not defined or they don’t constitute a valid path, the keystore is put in the JDK installation directory.
- • -storepass storepass—The passphrase for the keystore.
The default key size is 1024 bits and uses a key algorithm of DSA. Your Distinguished Name should follow the format
CN=Common Name OU=Organizational Unit ORG=Organization C=Country
For example, my Distinguished Name is
CN=Michael L Morgan OU=Software Engineering ORG=DSE Inc C=US
|





